
Sophos Home offers clear and easy to understand subscription pricing. We offer one- and two-year pricing options, and discounts for continuing customers. Renewals are done automatically at the end of the subscription period, with clear communication via email about upcoming renewal events.
The Internet Key Exchange is the protocol used to set up a security association (SA) in IPsec. The firewall supports IKE as defined in RFC 2409.
- 1 day ago We’ve completely redesigned the Sophos Firewall hardware to handle the modern encrypted internet. Security teams now have the ability to easily inspect encrypted traffic and shine light on what.
- Sophos has set the bar for security. Its products integrate seamlessly to better service a company’s whole environment.” Wil Craig, Head of IT, HydraFacial The Sophos Central platform is accessible from anywhere and this has greatly simplified things for us.”.
- Sophos Intercept X for Mobile is free, and it gives you additional protection not only against unsafe system settings and malware, but also helps to keep you away from risky websites in the first.
- Authentication (phase 1). During phase 1, the peers authenticate themselves using a preshared key or digital certificate. A secure, authenticated communication channel is created using the Diffie–Hellman algorithm to generate a shared secret key to encrypt further communications. This negotiation results in session keys and a security association.
- Key exchange (phase 2). In phase 2, the peers use the security channel established in phase 1 to negotiate an IPsec security association. The keying material for this association is created using the IKE phase 1 keys or by performing a new key exchange according to the PFS settings. This association encrypts the actual user data that is passed between the peers.
Diffie–Hellman key exchange
The Diffie–Hellman key exchange is a method of securely exchanging cryptographic keys over an insecure channel. The Diffie–Hellman algorithm was created to prevent secure encrypted keys from being attacked over the internet during transmission. Using the Diffie–Hellman key exchange with an authentication algorithm ensures protection against spoofing and man-in-the-middle attacks.
Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) is a method for deriving phase 2 keys independent from and unrelated to the preceding keys. When you specify PFS, a new key will be generated for every negotiation and a new DH key exchange is included. PFS offers improved security as it requires a network intruder to crack an additional key.
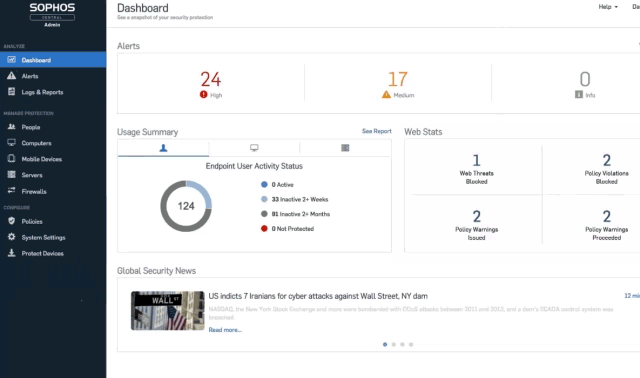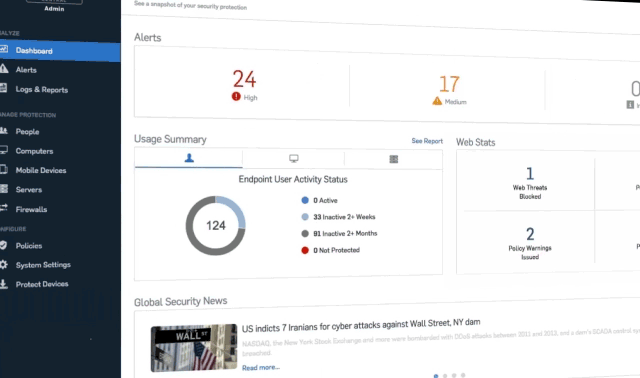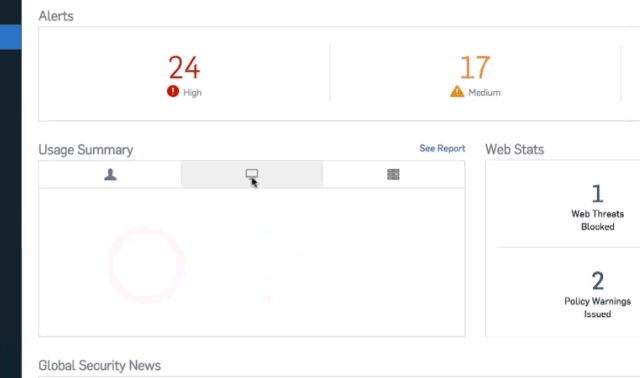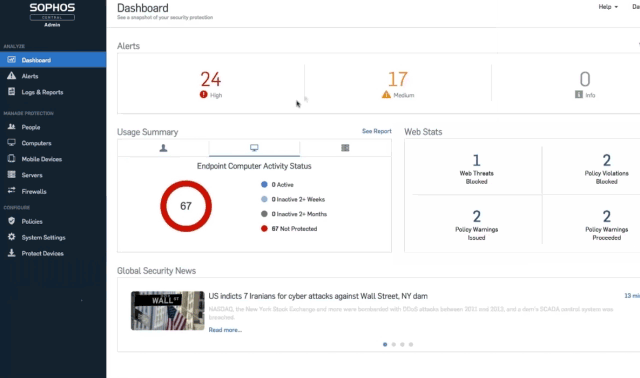
Gaining Internet activity insights and keeping abreast about security events is a challenging task as the security appliance generates a huge quantity of security and traffic logs. With a package of features, Firewall Analyzer's Sophos reporting capability fit like a glove enabling you to strengthen the network security. Firewall Analyzer lets you collect, archive, analyze Sophos device logs and generate security and forensic reports.
Sophos firewall security and capacity management
With Firewall Analyzer, a Sophos firewall monitoring toll, you can access predefined reports that help in analyzing bandwidth usage and understanding security and network activities. These reports help you to study the security vulnerability with top denied hosts, blocked URL hits, attacks, targets, virus, affected hosts, spam, receiving hosts.
Sophos firewall bandwidth capacity planning
Sophos firewall trend reports in Firewall Analyzer trace patterns in network behavior and bandwidth usage over time. Analysis of trend reports gives better insight into the nature of web site traffic or network traffic, and helps you make decisions on capacity planning, business risk assessment, bandwidth management, traffic shaping, and network security posture.
Sophos firewall bandwidth monitoring
Firewall Analyzer, a Sophos bandwidth monitor tool, provides a unique way to monitor the Internet traffic of the network in near real-time. Firewall traffic data is collected and analyzed to get granular details about the traffic across each firewall. There is no requirement for any probes or collection agents to get these details on the traffic.

Sophos Internet Security Review
Sophos traffic analyzer
Firewall Analyzer is a Sophos traffic monitor tool. It measures network traffic based on the analysis of logs received from different network firewalls. Firewall logs are collected, archived, and analyzed to get granular details about traffic across Sophos firewall devices.
Employee internet usage monitoring
With Firewall Analyzer for Sophos, you can maximize the business usage of Internet bandwidth using employee Internet monitoring. You can fine tune the Firewall policies to block or restrict bandwidth guzzling web sites and effectively control employee Internet usage. This will ensure that the bandwidth is available for smooth functioning of the business.
Sophos firewall alerts
Apart from exhaustive firewall reports with respect to network security, Firewall Analyzer offers comprehensive alarms and notifications.
The Sophos firewall log viewer tool generates alarms for anomalous security criteria, bandwidth values, and any normal criteria of security interest.
Alarms can be notified via email and SMS. It can trigger a script to achieve various threat mitigation activities. Alarms are also displayed in the UI screen.
To configure Sophos firewalls, refer the Sophos UTM and Sophos XG help pages.
Firewall Analyzer Sophos reports provide a unified solution to manage your organization's network security. The reports help you safeguard your network from external vulnerabilities. Download a 30-day free trial version of Firewall Analyzer today!
Sophos supported versions

Sophos Protection
| Company | Firewall/Version | WELF Certified | Other Log Format |
|---|---|---|---|
| Sophos | UTM 9.0 or later |
